Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
This category explains how publicly available information can be used to build digital profiles. It covers OSINT techniques, social media exposure, image analysis, and ways to reduce your digital footprint.
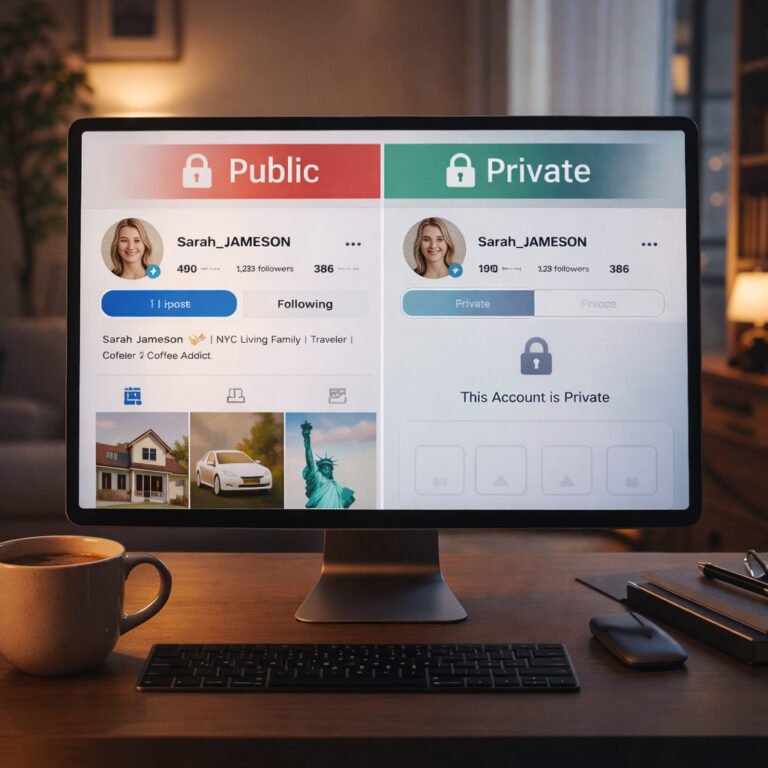
Private vs public social media is not a simple “one is safe, one is dangerous” question. In reality, both options come with trade-offs. A public profile can increase exposure, while a private profile can create a false sense of safety.…

How to use LinkedIn safely is a question more people should ask. LinkedIn is not just a “career platform” anymore — it is also one of the biggest OSINT databases on the internet. While Instagram and Facebook reveal your lifestyle,…
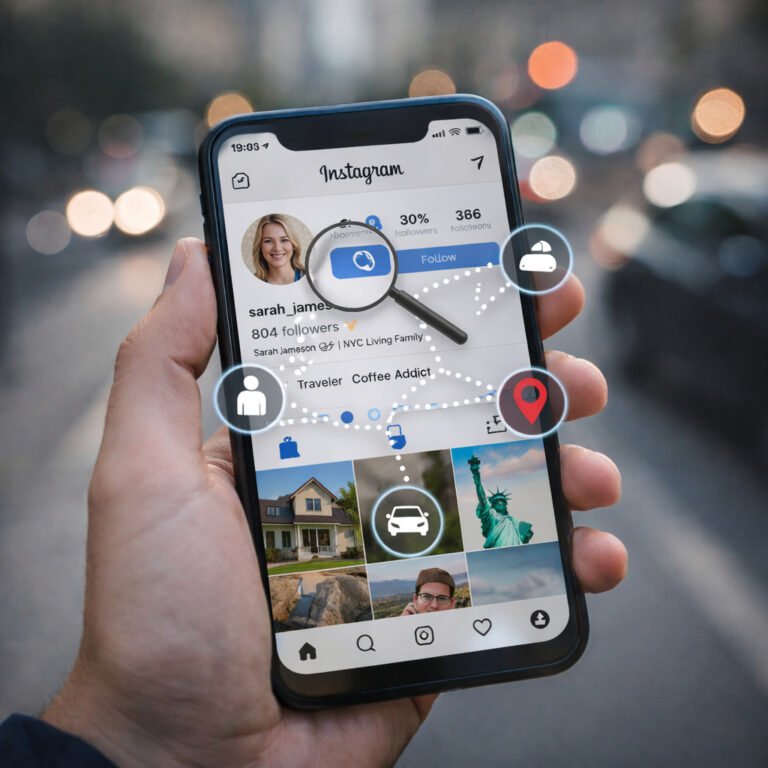
How criminals use social media is not a movie scenario — it’s a real-world OSINT technique used every day. Instagram and Facebook are not dangerous because of “hackers.” They are risky because people voluntarily publish patterns, locations, and personal details…

Why posting in real time is risky is not a paranoia topic — it’s one of the most practical online safety habits you can learn. The moment a Story, check-in, or “right now” post goes live, it may reveal your…

Posting a photo shouldn’t feel dangerous. However, in 2026, sharing pictures online can reveal far more than you think. If you care about online privacy security, this is one of the most important habits you can build. The good news?…

The term OSINT exposure describes how much information about you can be collected from publicly available sources such as social media, photos, comments, past accounts, online forums or leaked databases. Because people share more information today than ever before, reducing…

The idea of social media OSINT might sound abstract, yet it directly affects anyone who uses Facebook, Instagram, TikTok, X (Twitter), LinkedIn or any other platform. Because every post, like, comment, tag or story becomes part of a larger digital…

The phrase image OSINT may sound like something only investigators or cyber experts deal with, yet the reality is far more personal. Every photo you share — whether it’s a holiday snapshot, a gym selfie or a picture of your…

Cybercriminals increasingly rely on OSINT to plan attacks, manipulate victims and find weak spots long before they launch anything technical. Because open-source intelligence uses only publicly available information, criminals never need to hack a system to begin gathering details about…

The term OSINT (Open-Source Intelligence) has exploded in popularity, yet many people still misunderstand what it actually means. Because modern life takes place online, every post, photo and comment leaves behind a trace. When someone knows how to read these…