Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124

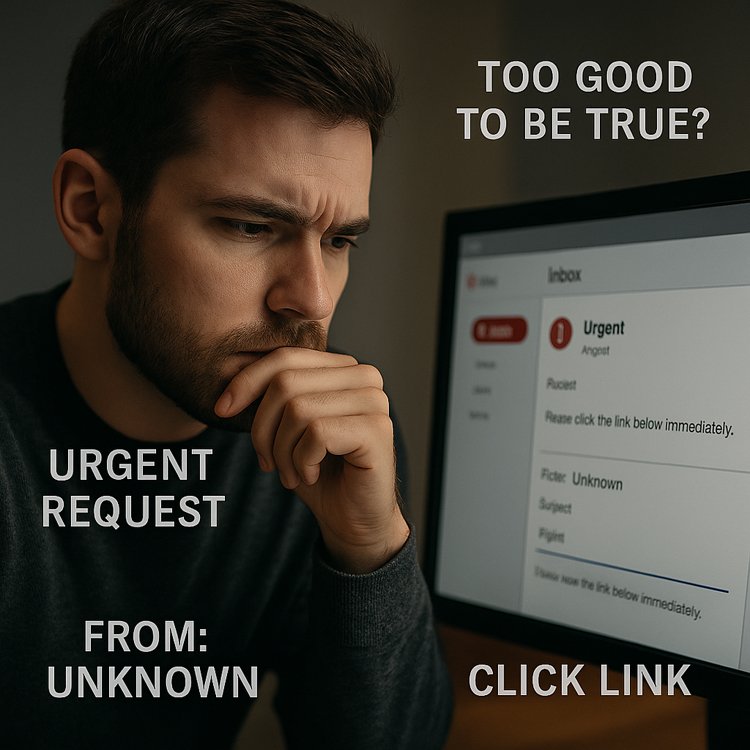
Phishing remains one of the most widespread cyber threats, and it continues to succeed because it targets human behaviour rather than technology. Although security tools have improved over the years, phishing still works because attackers exploit emotions like urgency, fear, curiosity and trust. In this guide, you’ll learn what phishing really is, why it stays so effective and how you can protect yourself in a digital environment full of distractions.…

The rise of deepfake porn has become one of the most troubling digital threats of the modern internet. What started as a fringe, experimental use of AI has transformed into a powerful weapon used for harassment, humiliation, blackmail, and revenge. Deepfake porn involves taking a real person’s face — often scraped from social media — and placing it onto explicit videos or images without consent. As AI models become more…

As deepfake technology continues to advance rapidly, deepfake identity theft has become one of the most alarming cyber threats of 2025. Criminals no longer need weeks of preparation, hacking skills, or expensive equipment to impersonate someone. Today, anyone with a smartphone and access to basic AI tools can clone a person’s face, voice, mannerisms, and online presence in less than an hour. This new reality dramatically expands the possibilities for…

The digital world is evolving fast, and one of the most concerning developments is the rise of deepfakes and children being directly or indirectly targeted by this technology. While deepfakes once focused on celebrities or political figures, 2025 has introduced a disturbing shift: children are increasingly appearing in AI-generated videos, manipulated images, voice clones, or fabricated scenarios designed to deceive, exploit, or emotionally manipulate families. Because children naturally share videos,…

As deepfake technology becomes increasingly convincing, learning how to spot a deepfake has become a basic digital survival skill. A few years ago, deepfakes were glitchy and easy to dismiss, yet in 2025 even simple tools can create incredibly realistic video calls, voice notes, and social media clips. Because scammers, cybercriminals, and misinformation actors rely heavily on deepfakes, identifying subtle manipulation is now more important than ever. Although AI-generated content…

As we enter 2025, deepfake scams have evolved from unusual tech curiosities into everyday cyber threats that target individuals, families, and businesses alike. Once limited to crude face swaps and glitchy fake audio, deepfake technology now produces highly realistic voices, videos, and images that can fool even cautious people. This rapid shift has created new opportunities for scammers and criminals who use artificial intelligence to impersonate loved ones, trick employees,…

The rise of deepfake technology has transformed online security faster than most people expected. Although it once seemed like a futuristic experiment, it has now become a daily threat affecting individuals, families, and organizations. Moreover, because deepfakes imitate reality so convincingly, they are quickly overtaking traditional scams that relied on poorly written messages or badly edited images. This article explains deepfakes in clear, simple language, while also showing why they…

Impersonation scams have become one of the fastest-growing online threats, and many families are urgently searching for practical ways to protect older adults from impersonation scams. Because criminals now use advanced tools such as AI voice cloning, caller ID spoofing and scripted emotional pressure, seniors often become their primary targets. Although this trend is worrying, families can dramatically increase safety by introducing simple habits that reduce panic, create clarity and…

The Problem With the “Nothing to Hide” Mindset Many people still believe, “I have nothing to hide.” On the surface, this appears logical — if you’re not doing anything wrong, why worry? Yet this “I have nothing to hide” cybersecurity mindset is both outdated and dangerous. It assumes privacy exists only for those with secrets, instead of recognizing privacy as a foundation of autonomy, dignity, and security. Moreover, privacy isn’t…
The human side of breach: why the psychology of hacking matters The psychology of hacking is simple and unsettling: hackers often don’t need to crack code when they can trick a person. In fact, social engineering and psychological manipulation are among the most effective attack methods because they exploit automatic human reactions — trust, curiosity, fear, and help-giving instincts. Understanding the psychology of hacking helps you see why a single…